Unlocking the Secrets of Veeam Hardened Linux Repository Part 1
Veeam Hardened Repository (VHR) is an option for secure, immutable backup storage and is a popular choice among Veeam enterprise customers.
However, IT security and Linux expertise are required to deploy and manage VHR properly over time. As such, it is unsuitable for environments lacking in-house IT security skills.
This blog post provides an overview of the pros, cons, and technical and operational considerations while choosing VHR for your environment.
How Ransomware is Reshaping Backup Security
Ransomware has changed the game of data protection. Simply backing up your data is no longer sufficient. Instead, you must also secure your entire backup environment from attack.
The explanation for this change is simple: criminals and hackers realized they had to remove their target’s ability to restore backed-up data for their extortion attempts to succeed.
It is plausible to assume that these bad actors even went so far as to become certified in different backup solutions to enhance their expertise at compromising these systems.
Combating Ransomware with Veeam's Hardened Linux Repository
Veeam developed a solution to help counter this growing threat. The Veeam Hardened Repository can raise defenses against ransomware by securing backup data without compromising performance.
The solution leverages the Linux XFS file system, which supports data cloning to save space like Windows REFS file systems and is based on two solid security principles: single-use credentials and immutability.
The Role of Single-Use Credentials and Immutability in VHR
The credentials to deploy Veeam software are used only once during the installation of the Veeam components, after which they are discarded and are not stored in Veeam’s credential database.
Immutability means that files are written and marked immutable and cannot be changed or deleted until the immutability lock has been removed (so long as the server root access is not compromised).
Immutability is achieved by leveraging the XFS file system immutability bit in the file. It is not a new technology but has gained much more importance since the emergence of ransomware.
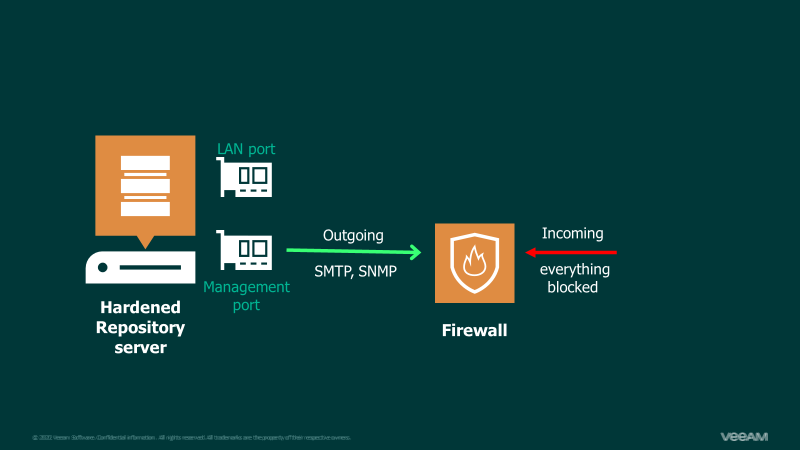
Anyone with root privileges on the server can change or remove the immutability setting and then delete or modify the data. It makes hardening and restricting root and physical server access a critical priority in the environment’s design. Any break-in to the administrator’s access renders the solution vulnerable to data destruction.
It is also important to mention that virtual VHR setups are insecure. While they can create immutable storage inside the repositories, they also open a large attack surface at the hypervisor and storage access levels.
Regarding hardware, most server configurations, including Dell, HPE, and Cisco, are all acceptable solutions for a VHR. Remember to fully secure the console and firmware access and pay close attention to add-on management or monitoring software, as these further expand the security attack surface.
Key Maintenance Practices for Veeam Hardened Linux Repository
The Veeam Hardened Repository can be an excellent solution, but installing and maintaining it properly requires Linux and security expertise. Veeam provides detailed setup instructions to get the VHR up and running.
Still, one must further harden the operating system, physical access, and console access through tools like IPMI and ILO/IDRAC and continually monitor for software updates, vulnerabilities, and exploits.
Software changes to the VHR environment must be tested to ensure the continued proper operation of VHR and its security. Therefore, the backup administrators should work closely with your in-house security team to ensure the deployment is kept secure, continuously monitored, and functioning well for backup operations.
Ootbi's Impact on Overcoming VHR Operational Challenges
For many large enterprises with the necessary IT security personnel, the VHR-required procedures can be performed continually. However, the Veeam Hardened Repository will become an operational and security challenge for other environments.
In such cases, vendor solutions like Object First’s Ootbi (out-of-the-box immutability) are better suited because the responsibility of maintaining and ensuring the security of the backup repository is mainly shifted to the vendor and not solely to the backup administrators.
Ootbi is secure, simple, and powerful, providing a hardened object storage target with optimal performance purpose-built for Veeam. Administrators cannot delete or modify immutable data, nor can cybercriminals if they gain access to the administrator’s credentials.
Request a demo to see how out-of-the-box immutability can be achieved in 15 minutes for your Veeam data protection environments with much less effort and responsibility required from your IT team.
