Zero Trust and Enterprise Data Recovery
The Zero Trust model represents the current best practice for organizations seeking to protect and secure their data and business. However, this model has not been substantively applied to data backup and recovery. Zero Trust advisory firm Numberline Security and Veeam recently collaborated on research to fill this gap and reduce risk for organizations seeking to evolve beyond perimeter security. Their research resulted in the new Zero Trust Data Resilience (ZTDR) model.
Zero Trust Data Resilience builds on the Cybersecurity and Infrastructure Security Agency's (CISA) Zero Trust Maturity Model (ZTMM) as a foundation, extending its principles to data backup and recovery. The Zero Trust Data Resilience framework is a practical guide for IT and Security teams to improve data protection, reduce security risk, and enhance an organization’s cyber resilience.
This blog series provides a holistic overview of ZTDR and helps understand why it should be implemented in every backup and recovery architecture.
Zero Trust Principles
Zero Trust is a security paradigm replacing the more traditional and increasingly ineffective perimeter-based security approach. Zero Trust is being adopted as the best-in-class IT security standard by the US government and enterprises worldwide.
Zero Trust is universally applicable to organizations that operate on-premises, in the cloud and hybrid environments, and to enterprises of different sizes and across industries.
The primary principles of Zero Trust include:
- Assume a breach. Segment access to the most critical data assets to minimize the attack surface and blast radius.
- Verify explicitly. Always authenticate and authorize by leveraging Identity and Access Management (IAM) context (location, time, etc.) and strong MFA-based authentication.
Use least-privilege access for every user, device, and application.
In addition, Zero Trust mandates continuous security visibility and analytics, automation and orchestration, and governance for data lifecycle management.
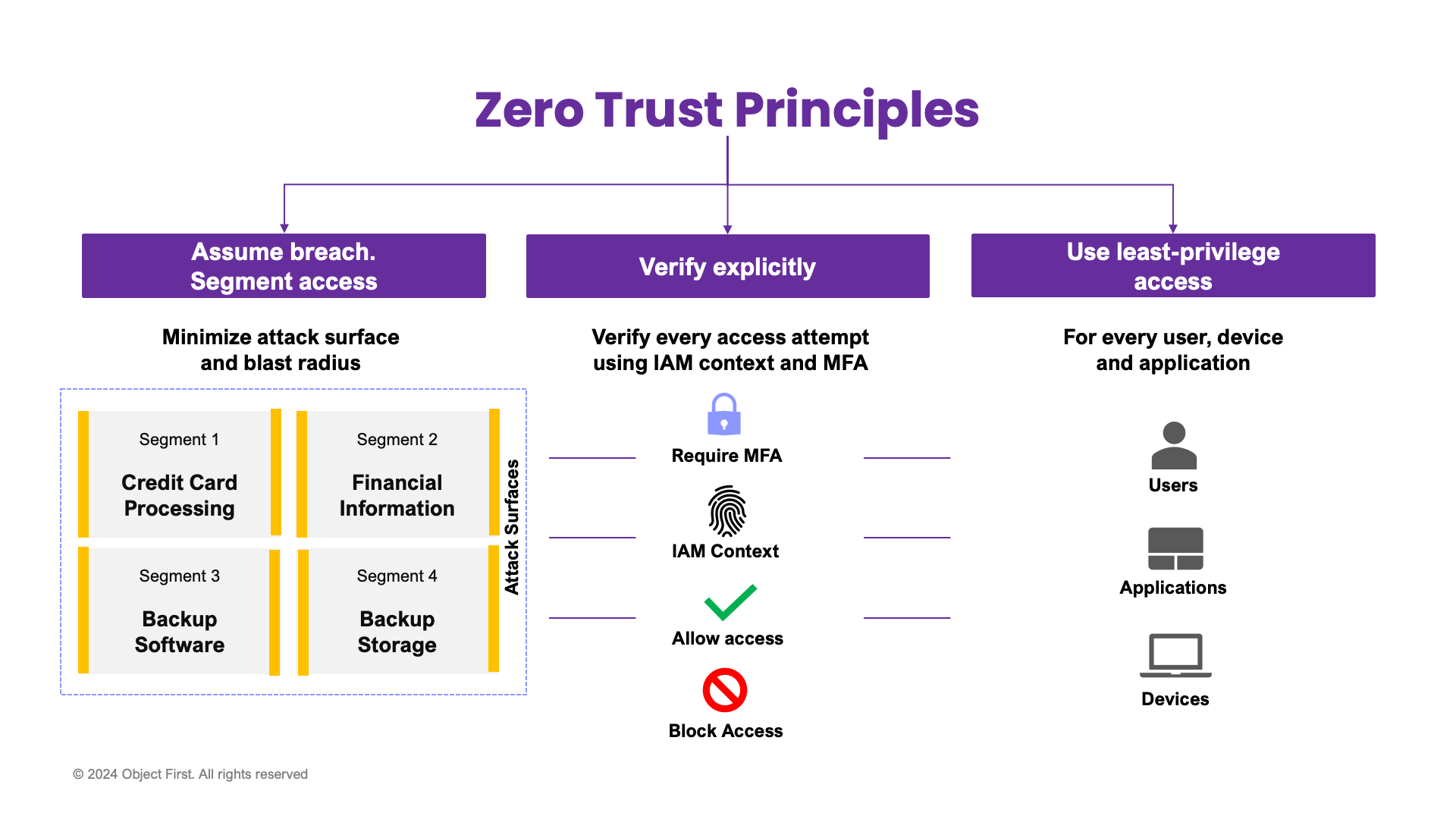
Figure 1: Zero Trust Principles
The Zero Trust Maturity Model - the standard framework for Zero Trust application
The de facto standard framework for looking at Zero Trust is the CISA's Zero Trust Maturity Model, depicted in Figure 2, which defines five core pillars: Identity, Devices, Networks, Applications & Workloads, and Data. It also defines three cross-cutting capabilities: Visibility and Analytics, Automation and Orchestration, and Governance.
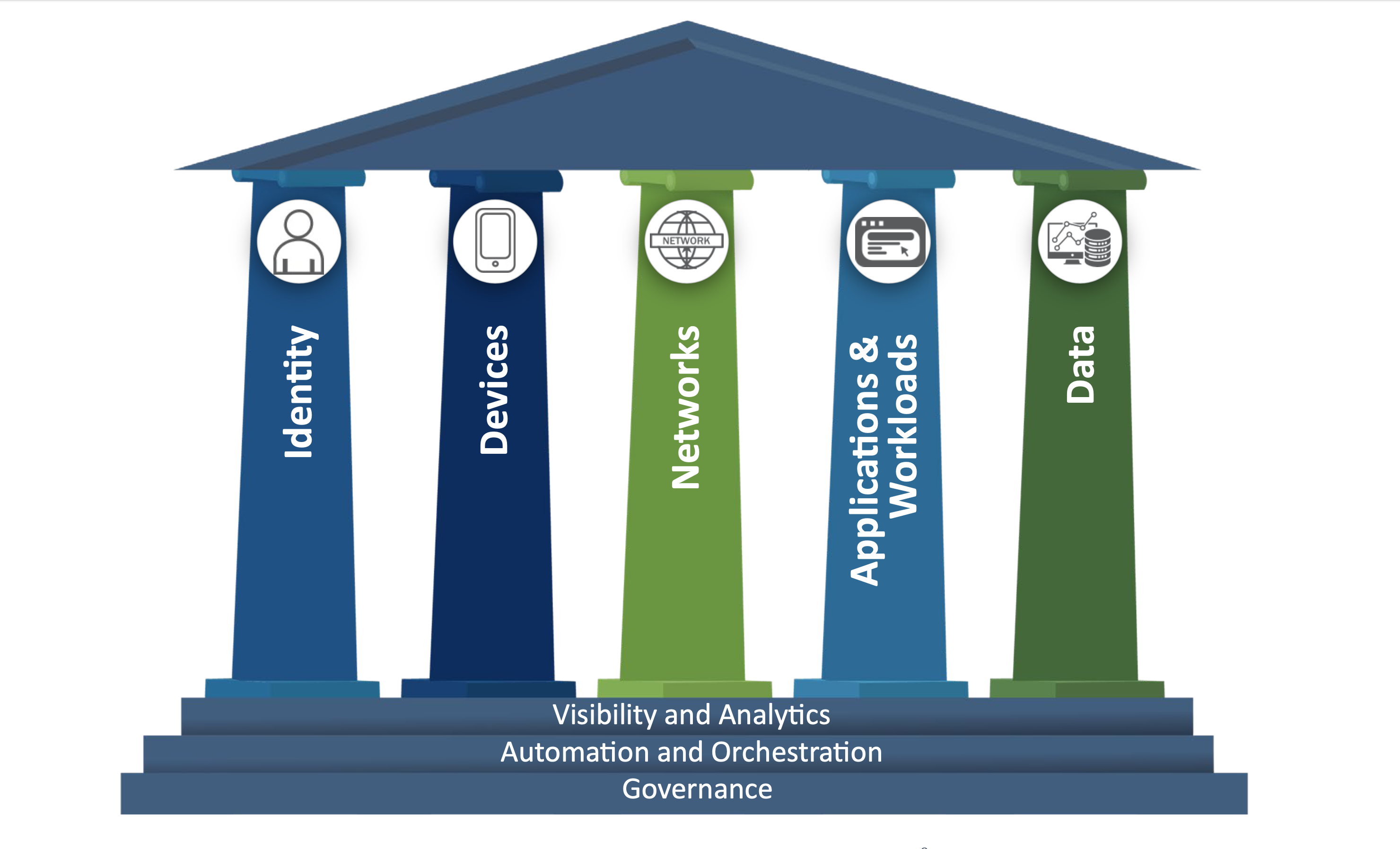
Figure 2: Zero Trust Maturity Model
Zero Trust Maturity Model limitations
Within the Data pillar of its Zero Trust Maturity Model, CISA identifies five further functions:
- Data Inventory Management.
- Data Categorization.
- Data Availability.
- Data Access.
- Data Encryption.
However, the CISA Zero Trust model is silent on requirements and maturity levels for data backup and recovery systems. Because this area is so essential for enterprise confidentiality, integrity, and availability, we believe this gap must be addressed.
To address this issue, Veeam and Numberline introduced Zero Trust Data Resilience, which includes principles, a reference architecture, and a new set of capabilities for the Zero Trust Maturity Model.
Zero Trust Data Resilience (ZTDR) Principles
Zero Trust Data Resilience research introduces the following ZTDR principles extending Zero Trust to Enterprise Data Backup and Recovery:
- Segmentation — Separation of Backup Software and Backup Storage to enforce least-privilege access, as well as to minimize the attack surface and blast radius.
- Multiple data resilience zones or security domains to comply with 3-2-1 Backup Rule and to ensure multi-layered security.
- Immutable backup storage to protect backup data from modifications and deletions. Zero access to root and OS, protecting against external attackers and compromised administrators is a must-have as part of true immutability.
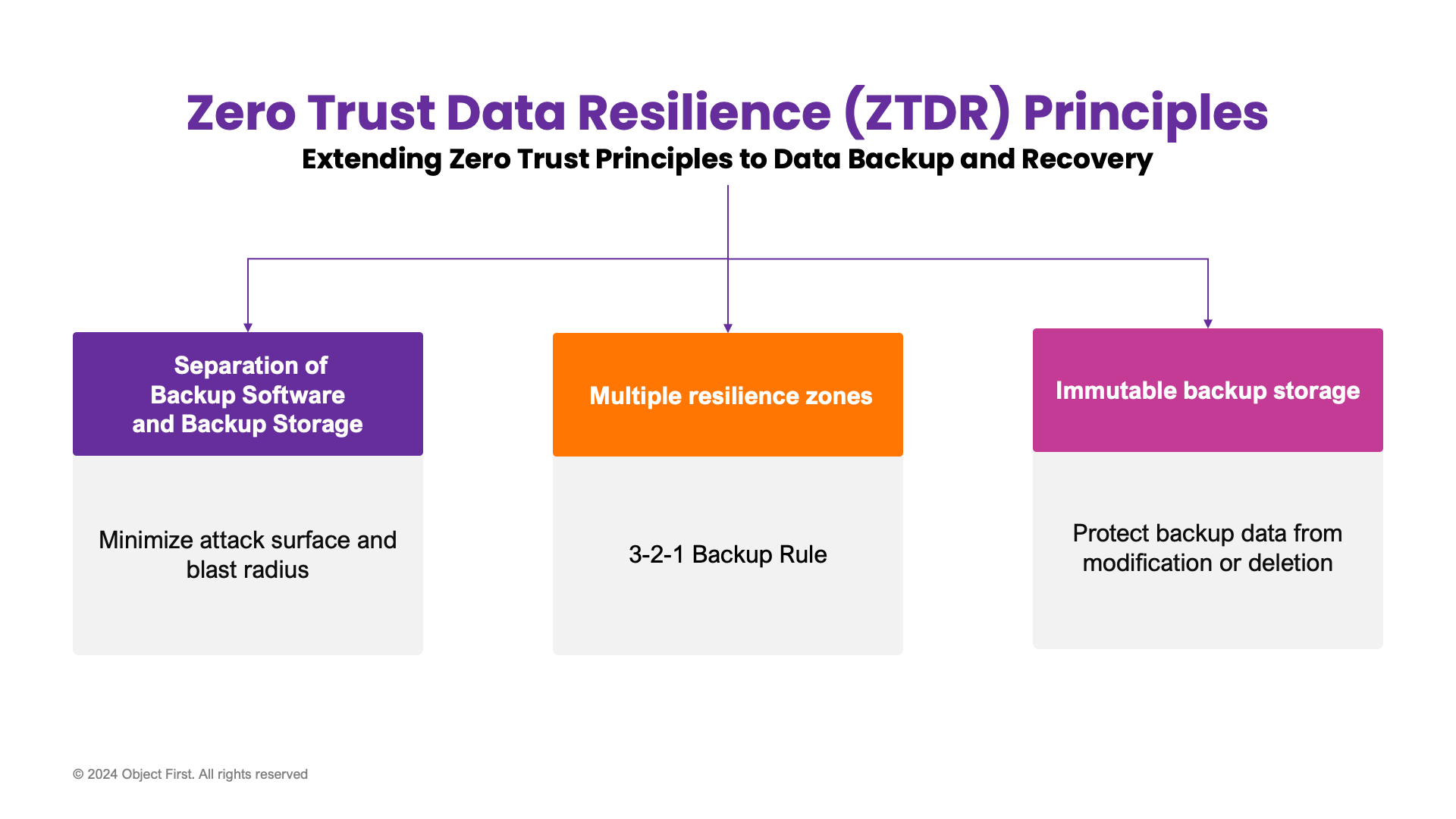
Figure 3: ZTDR principles
Zero Trust Data Resilience (ZTDR) is the latest and most secure backup architecture that extends the principles of ZTMM to address the backup and recovery use case.
By embracing ZTDR, organizations will have a clear and concrete pathway to strengthening their security posture. This means more efficient operations and alignment between IT and security teams, ultimately leading to a faster and safer recovery.
This blog series delves further into ZTDR principles.



