How Secure is VHR Really?
How to Apply Secure Design to Data Protection Architecture
Why would anyone willingly board a plane? After all, traveling 600 mph at an altitude of 40 thousand miles in a highly flammable tin can seems like the least safe mode of transportation.
And yet, everybody knows the opposite is true. Aviation defies a multitude of threats by doubling down on security. As a result, flying is officially the safest form of travel.
Can you make a similar claim about your data protection architecture?
IT Security and Backup
In this article, we’ll look at IT security in backup architecture as a continuous process that needs to be constantly revisited.
As threats change and adapt, no single security measure can be taken for granted as a one-size-fits-all. That’s why at Object First, we follow specific frameworks to make sure that Object First Ootbi (Out-of-the-box Immutability) is not only the best storage for Veeam, but also complies with the latest security standards, remaining consistently secure, simple, and powerful.
Read on to find out more about our process and backup security in general.
How Secure Is Your Veeam Backup Repository?
If you’re feeling adventurous and want to test your backup security, try this exercise: send fake phishing emails to your employees and see how many fall for the trap. It’s likely not going to be zero.
A system is not secure when it can never be breached, but when it’s designed with breaches in mind.
From the point of view of IT security, it doesn’t matter if people click the malicious link in a phishing simulation. What matters is getting prepared for when they do–by implementing custom precautions explicitly designed to counteract this kind of incident.
That’s the domain of IT security: developing strategies to prevent and mitigate potential data incidents, such as ransomware.
Oh, right, ransomware–the archnemesis of backups. Did you know that ransomware targets backups 9 times out of 10? Criminals know they won’t get paid if you can restore the data they encrypted for ransom.
However, encryption or destruction is only what ransomware does once it has penetrated the perimeter.
To be truly ransomware-proof, don’t wait until you have to stop the encryption. Segment the infrastructure to contain the infiltration.
How Can Ransomware Be Delivered?
This question should underpin the design of every ransomware-proof backup repository. We can use it to anticipate various ways that ransomware can get inside our systems. These ways may include:
- Social engineering, also known as phishing, may take many forms–a good old email, a pop-up, a phone call, or even a Wi-Fi clone.
- Insider threats. Disgruntled employees are a growing force behind security incidents. In fact, insider threats account for 31% of data breaches.
- Stolen credentials. According to a report by Mandiant, 40% of ransomware attacks in 2023 used compromised credentials as the attack vector.
- Human error. The evergreen of liabilities and human error always makes the list of top security risks.
Designers and engineers must identify these and other threats to their backup infrastructures and follow up with effective solutions. Only then can they create a robust and secure backup appliance.
Backup Appliance Best Practices
Ootbi, which stands for out-of-the-box immutability, is a backup appliance purpose-built for Veeam by Veeam’s founders.
Since our launch in 2022, ransomware remains top-of-mind for IT specialists, and backups remain the best way to protect your data.
However, threat actors and their methods have evolved. To keep up, we are evolving with them.
For example, immutability has always been our core value. Eventually, though, we had to ask ourselves: does immutability alone address the current security challenges, or should we add something to it to account for other threats?
Is Immutability Always a Good Thing?
Yes, we’re being provocative. After all, immutability has always been vital to our business. It’s even in the name of our product.
Then again, the term “immutability” has dominated the discourse in cybersecurity so completely that it may make us oblivious to other threats–ones that immutability cannot address.
Remember: immutability is only the last line of defense. When it stops a malicious agent from encrypting your backups, there’s hardly a reason for celebration. That agent has been roaming around your premises for quite some time. All the other defenses have failed, which means the security of your data hangs by the thin thread of immutability alone.
When immutability stops ransomware, it means all the other defenses failed. Don’t pin your data security on immutability alone.
It’s as if your only security assurance on board a cruising plane was a small parachute precariously wrapped around your arms.
Threat Modeling and Secure Design Principles
Enter threat modeling and secure design principles. These security frameworks were developed by OWASP, The Open Worldwide Application Security Project, an international charity with two decades of experience in promoting security best standards.
What is the purpose of threat modeling and secure design principles?
OWASP developed threat modeling and secure design principles to help engineers equip their systems with powerful, relevant, and effective defense mechanisms.
Engineers use threat modeling and secure design principles as inspiration for devising defense mechanisms.
These mechanisms are not supposed to be arbitrary. There isn’t a laundry list of “10 things every system must have to be secure.” Instead, threat modeling and secure design principles are recommendations–or prompts. Designers and engineers use these prompts to develop security measures specific to their needs. For example, they can extend their arsenal of ransomware defense beyond immutability.
Let’s examine the two security frameworks and their application to backup, starting with threat modeling.
What is threat modeling in cybersecurity?
In cybersecurity in general and in backup architecture design specifically, threat modeling revolves around four key questions. Engineers ask them before sitting down at the drawing board. Ideally, though, they will never stop asking them.
IT security is a continuous process, so the four questions can never be definitively answered.
Threat modeling asks questions you can never definitively answer. IT security is a moving target, so the answers will always change.
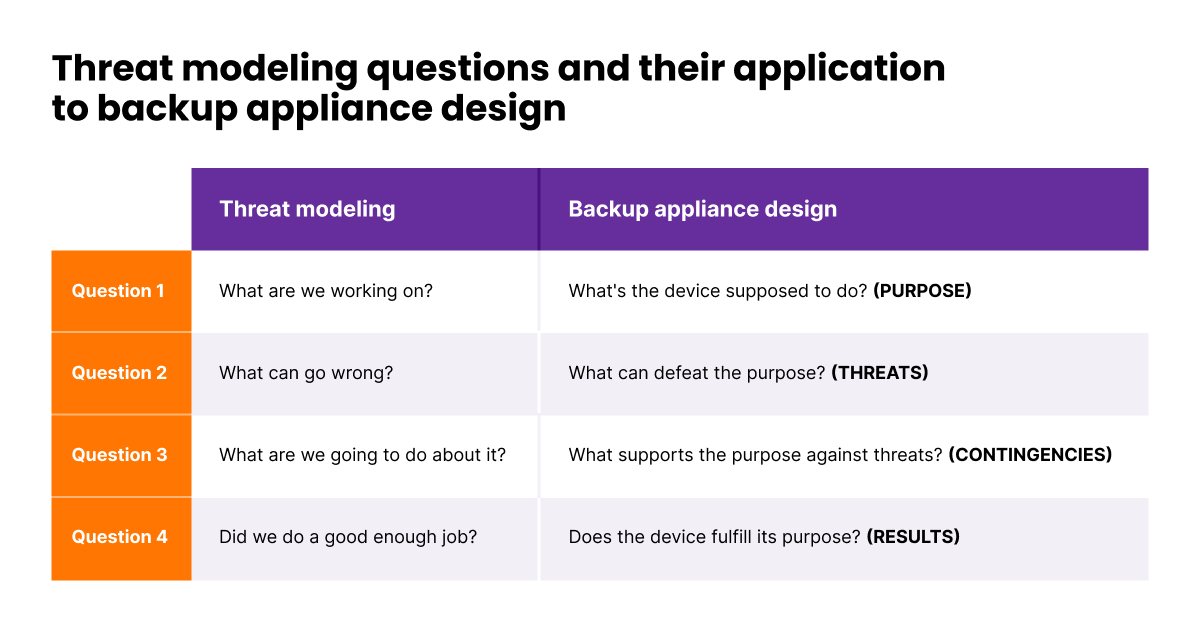
Fig. 1. Threat modeling questions and their application to backup appliance design
Note that we’ve made all the questions about purpose. That’s because purpose is our ultimate measure of success and a key principle behind design and execution at Object First.
Also, experience tells us that a clearly defined purpose helps answer the other threat modeling questions more accurately.
How to Do Threat Modeling for Backups?
A closer look at our product description will make apparent our purpose in creating Ootbi:
Ransomware-proof and immutable out-of-the-box, Ootbi by Object First delivers secure, simple, and powerful backup storage for Veeam customers.
The product description highlights immutability, data integrity, and ransomware resilience as Ootbi’s key security features.
Now, the threat model forces us to consider: What can undermine Ootbi’s immutability? What can compromise its data integrity? What can decrease its ransomware resilience?
With a mix of imagination and experience, we come up with plausible threat scenarios. Then, it’s time to research, ideate, engineer, and implement solutions to mitigate those scenarios.
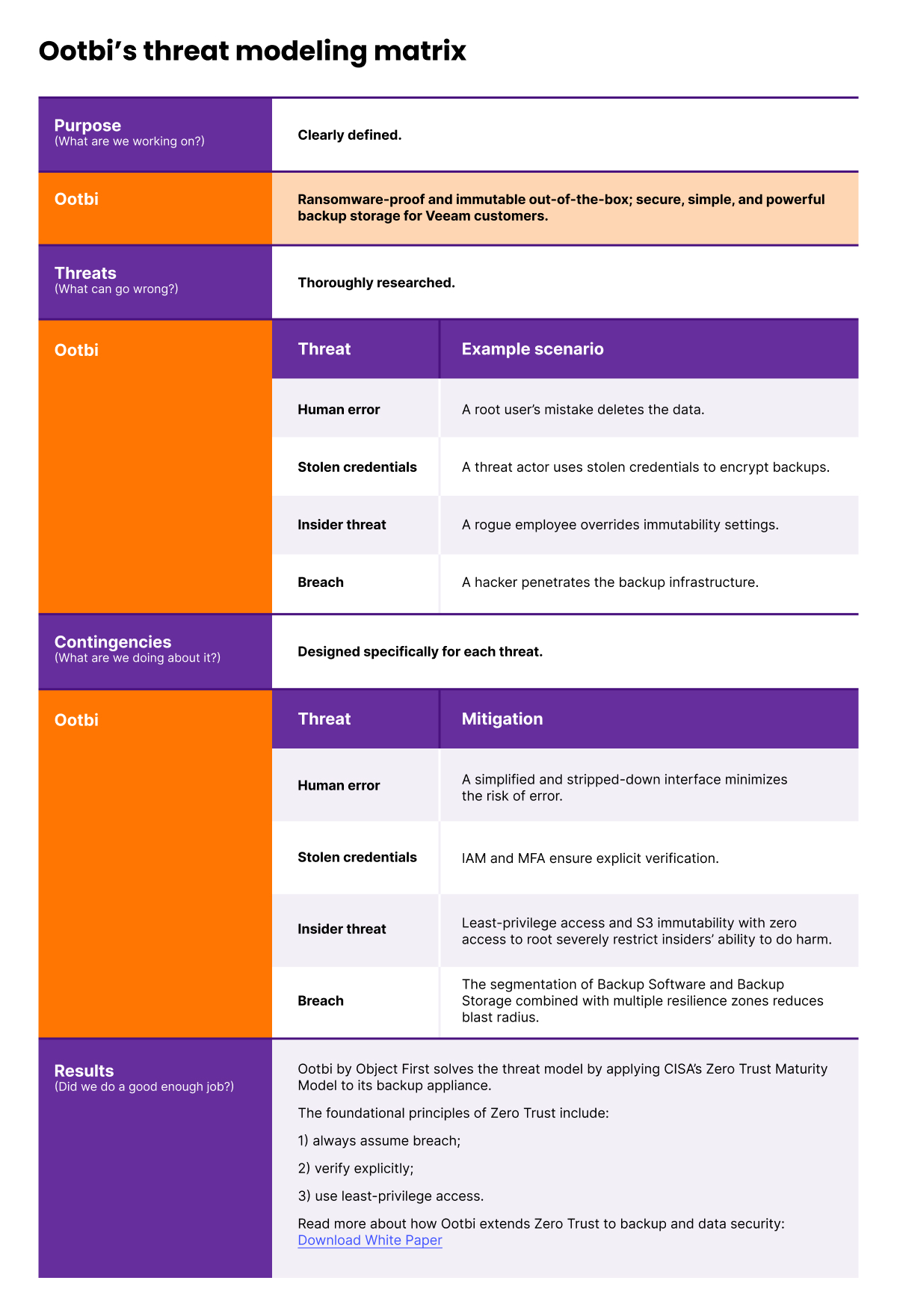
Fig. 2. Ootbi’s threat modeling matrix
Let’s now move on to the other framework developed by OWASP: secure design principles.
What Are the Principles of Secure Design?
Like threat modeling, secure design principles support the creation of secure products. However, while threat modeling offers a set of open-ended questions, secure design principles are a bit more prescriptive.
Every principle addresses a particular security pitfall. These pitfalls are largely universal. For example, avoiding a single point of complete compromise sounds reasonable whether you’re building a backup appliance or a plane.
Secure design recommendations are universal whether you’re building a backup appliance or a plane.
For every such pitfall, secure design principles propose a broad recommendation, e.g., “A single point of complete compromise can be avoided with multiple security controls.” However, what security controls are utilized and how they should be implemented is a matter of choice and best left to seasoned security experts.
The principles don’t prescribe specific implementations. This decision is best left to security experts.
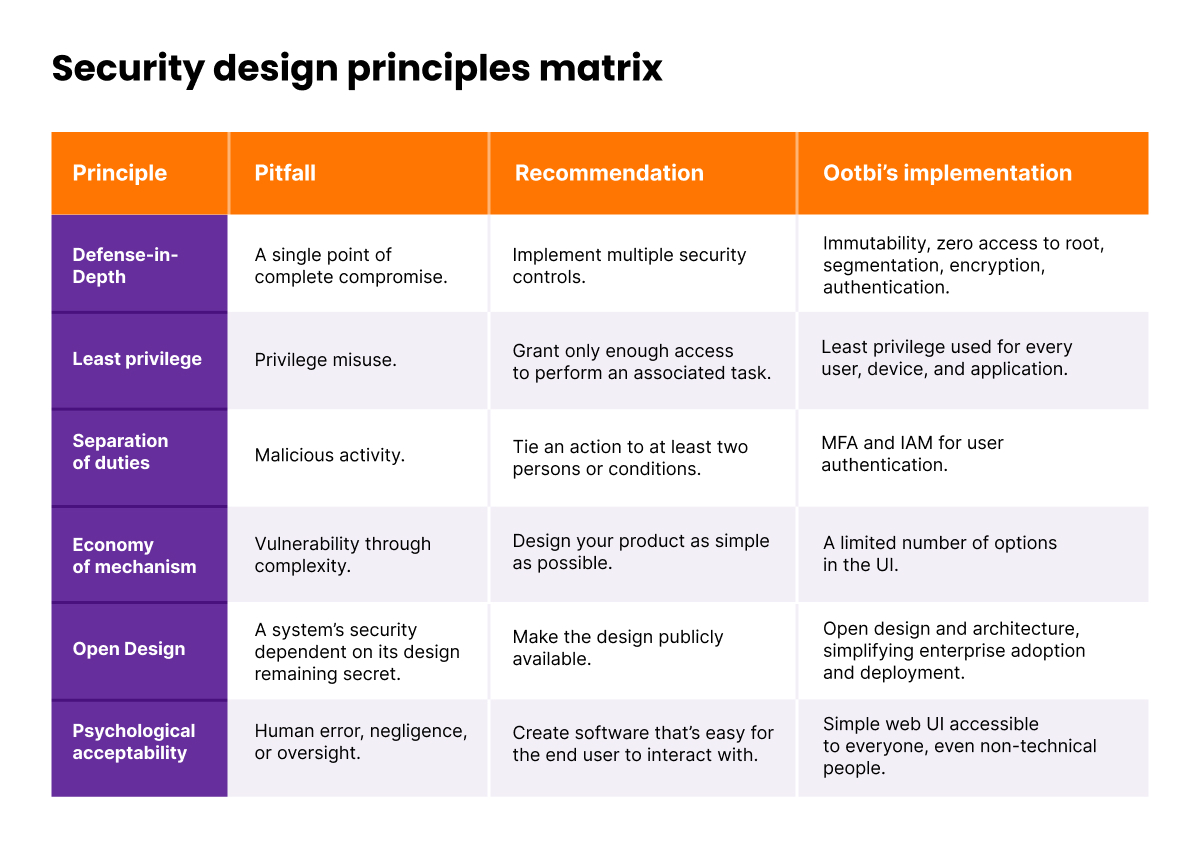
Fig. 3. Security design principles matrix
Ootbi: Continuously Vetted by Experts in the Field
Theoretically, all you need for backups is Linux and storage. Combine the two with a bit of admin magic, and you get yourself a hardened Linux repository.
Is your hardened Linux repository going to be as hardened a year from now?
Airplanes are manufactured under supervision and according to construction standards. They regularly undergo maintenance, security checks, and upgrades. You wouldn’t expect to fly in a do-it-yourself plane even if you had an instruction manual and parachute to go with it.
Like aviation, data security is not for the DIY-minded. If you care about your backups, there’s only one way to be sure they’re exactly as safe in a year as they are today: hiring professionals.
Object First continuously applies threat modeling and secure design principles to Ootbi.
Object First applies threat modeling and secure design principles to Ootbi on an ongoing basis. We release software updates and offer 24/7 support so the user doesn’t have to think about configuration, maintenance, or adaptation to the ever-changing threat landscape. We do all of that for them.
Request a demo today and see how Ootbi by Object First continuously upholds the latest security standards. With Ootbi, the most secure repository for Veeam, you don’t have to worry if your data protection architecture is up to date: it always is.



