3 Zero Trust Principles for Data Backup
In blog #1 of this series, we have outlined Zero Trust principles and introduced the new Zero Trust Data Resilience (ZTDR) model. The ZTDR model and architecture have been developed in collaboration between Veeam and Numberline Security. It extends the tenets of CISA’s Zero Trust Maturity Model with the following principles that cover enterprise data backup and recovery (see Figure 1):
- Segmentation — Separation of Backup Software and Backup Storage to enforce least-privilege access, as well as to minimize the attack surface and blast radius.
- Multiple data resilience zones or security domains to comply with the 3-2-1 Backup Rule and to ensure multi-layered security.
Immutable backup storage to protect backup data from modifications and deletions. Zero access to root and OS, protecting against external attackers and compromised administrators, is a must-have as part of true immutability.
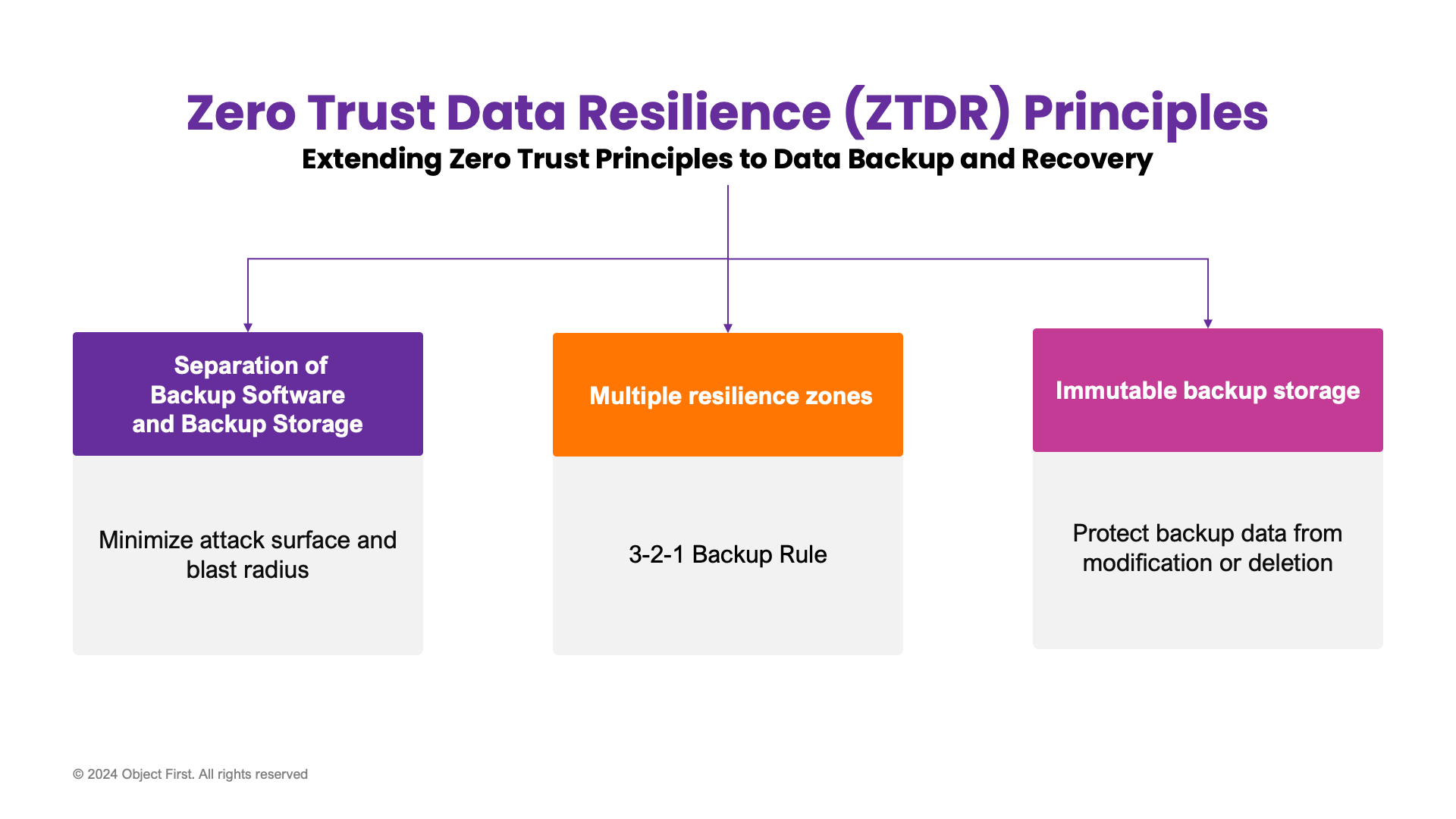
Figure 1: ZTDR foundational principles
In this blog, #2 of the series, we will examine the three (3) principles of Zero Trust Data Resilience in depth.
Principle #1: Segmentation of Backup Software and Backup Storage
Backup infrastructure inherently has a large attack surface, requiring read and write access to production systems across all enterprise applications and data sources for both on-premises and hybrid cloud environments. To mitigate this risk, Zero Trust Data Resilience requires that backup infrastructure is segmented into multiple resilience zones or security domains — such as Backup Software, Primary Backup Storage, and Secondary Backup Storage – each with its least-privileged access, reduced attack surface, and minimal blast radius. In this case, the Backup Software may still have an exposed attack surface, but the Backup Storage will have a minimal attack surface. This is achieved by using Zero Trust access control and a secure communication protocol such as S3 over HTTPS to minimize the risk of penetration to the Backup Storage component (See Figure 2).
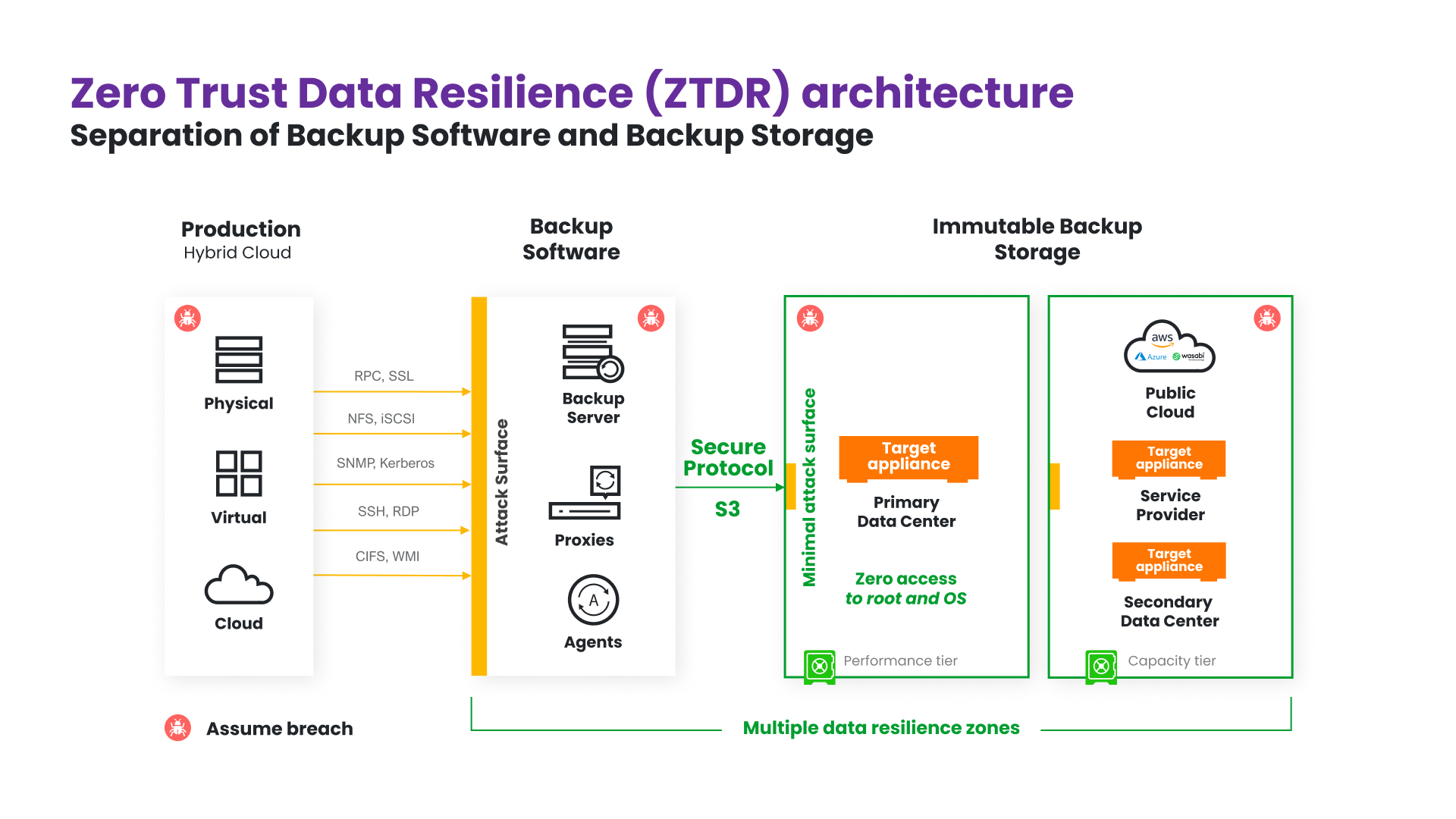
Figure 2: ZTDR architecture
Principle #2: Multiple Data Resilience Zones
A core Zero Trust concept for networking is microsegmentation to break up security perimeters into smaller zones, to enforce least-privilege access, and to reduce the blast radius of any compromised zone and the lateral movement of an attacker. For ZTDR, this concept can be applied by using data resilience zones. Resilience zones separate backup storage and isolate the storage control plane from the backup software and its control plane. This provides a critical line of demarcation that ensures backup data survivability even in the event of compromised backup software. This can happen for a multitude of reasons, including internal bad actors. A backup system must ensure that backup data can be simply and quickly recovered from a clean install of the backup software. Multiple data resilience zones safeguard the efficacy of the multi-layered security strategy and your compliance with the 3-2-1 Backup Rule.
3-2-1 Backup Rule
- At least three (3) copies of data including production data.
- At least two (2) copies of backup data on immutable storage in separate resilience zones.
- At least one (1) copy off-site.
Principle #3: Immutable Backup Storage
According to ZTDR, backed up data must also be immutable so that even in the event of a ransomware attack, backed up data cannot be modified or deleted. Data resilience can be maximized by providing customers with a hardened, immutable storage target set to compliance mode with zero access to the operating system or root account. This storage can include vendor-specific solutions and protocols and industry-standard protocols like S3 used by Object First.
S3-native Immutability and Security
- S3 provides the most trusted industry-standard storage immutability, security, IAM and secure communication protocol.
Open Design and Architecture
- Open Design and Architecture is one of the fundamental principles of IT security in general. Using industry-standard S3 protocol aligns well with this principle.
Conclusion
A well-architected data backup and recovery system will include segmentation between the Backup Software and Backup Storage layers. This is the major principle of ZTDR and is directly derived from the main Zero Trust principle of access segmentation. This segmentation is critical to maintain the resilience, immutability, and flexibility enterprises need. It reduces the attack surface and ensures multi-layered security, dramatically reducing the data breach risk.



