Not Zero Trust Backup Architectures
In blog #2 of this series, we delved into the central principles of the Zero Trust Data Resilience (ZTDR) model: segmentation, multiple data resilience zones, and immutable backup storage. This model and architecture, a collaborative effort between Veeam and Numberline Security, extends CISA’s Zero Trust principles and Maturity Model to the enterprise data backup and recovery use case (see Figure 1):
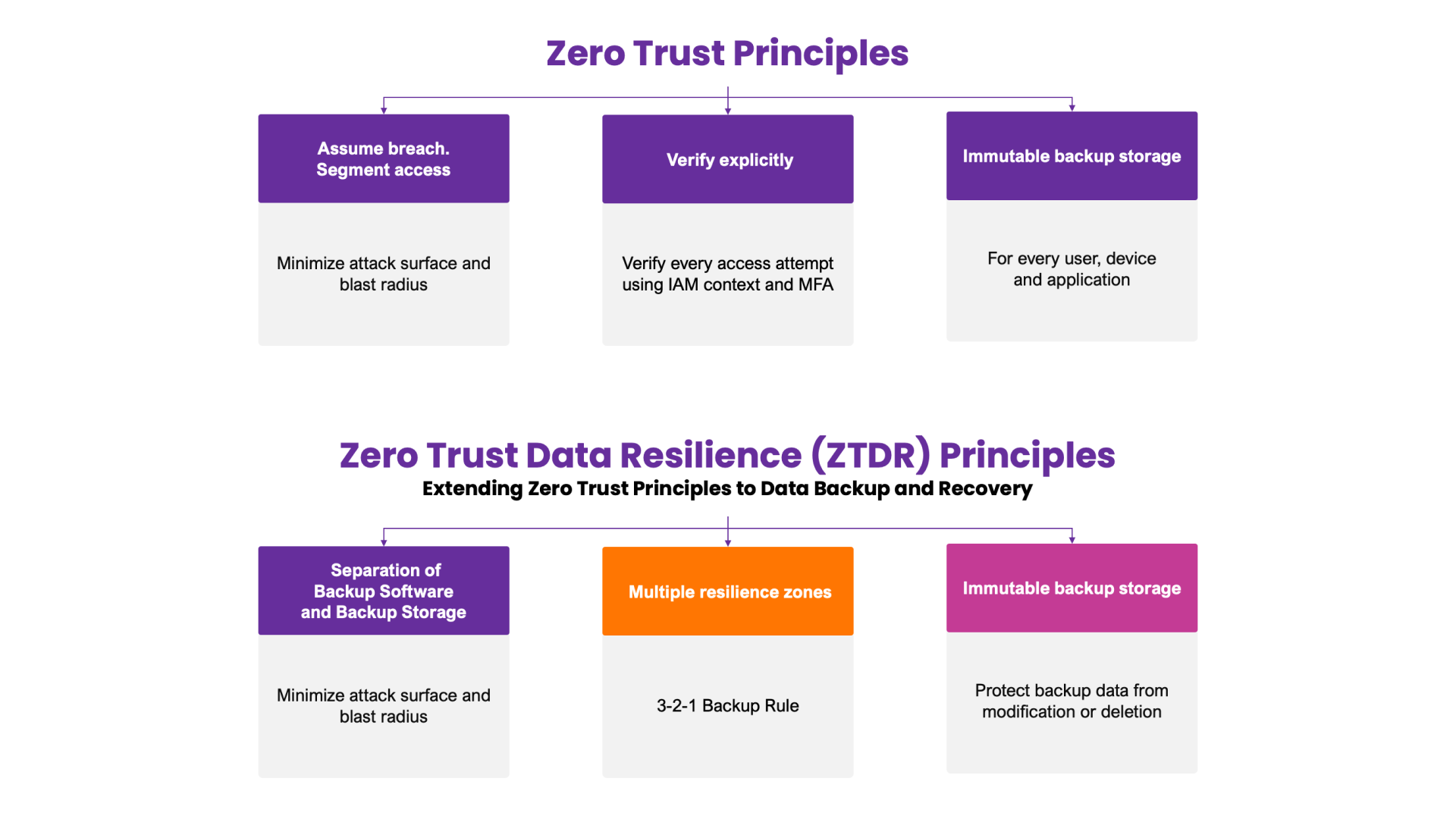
Figure 1: ZTDR foundational principles
Now that we have covered the principles of ZTDR and how it helps you secure backup infrastructure, let’s examine non-Zero Trust architectures and pinpoint some security pitfalls they create.
Monolithic (Integrated) Appliance - Not Zero Trust
It is crucial to consider the backup architecture you choose for your organization's data resilience needs. One example to consider is the monolithic or integrated appliance. This architecture does not meet the requirements of Zero Trust Data Resilience because there is no separation between backup software and backup storage (see Figure 2). Any attacker would have full access to backup software and storage in a breach. As a result, true immutability cannot be achieved, and the attacker can modify, delete, or render backup data inaccessible. The backup and recovery system would be compromised entirely, creating a significant blast radius for the attack.
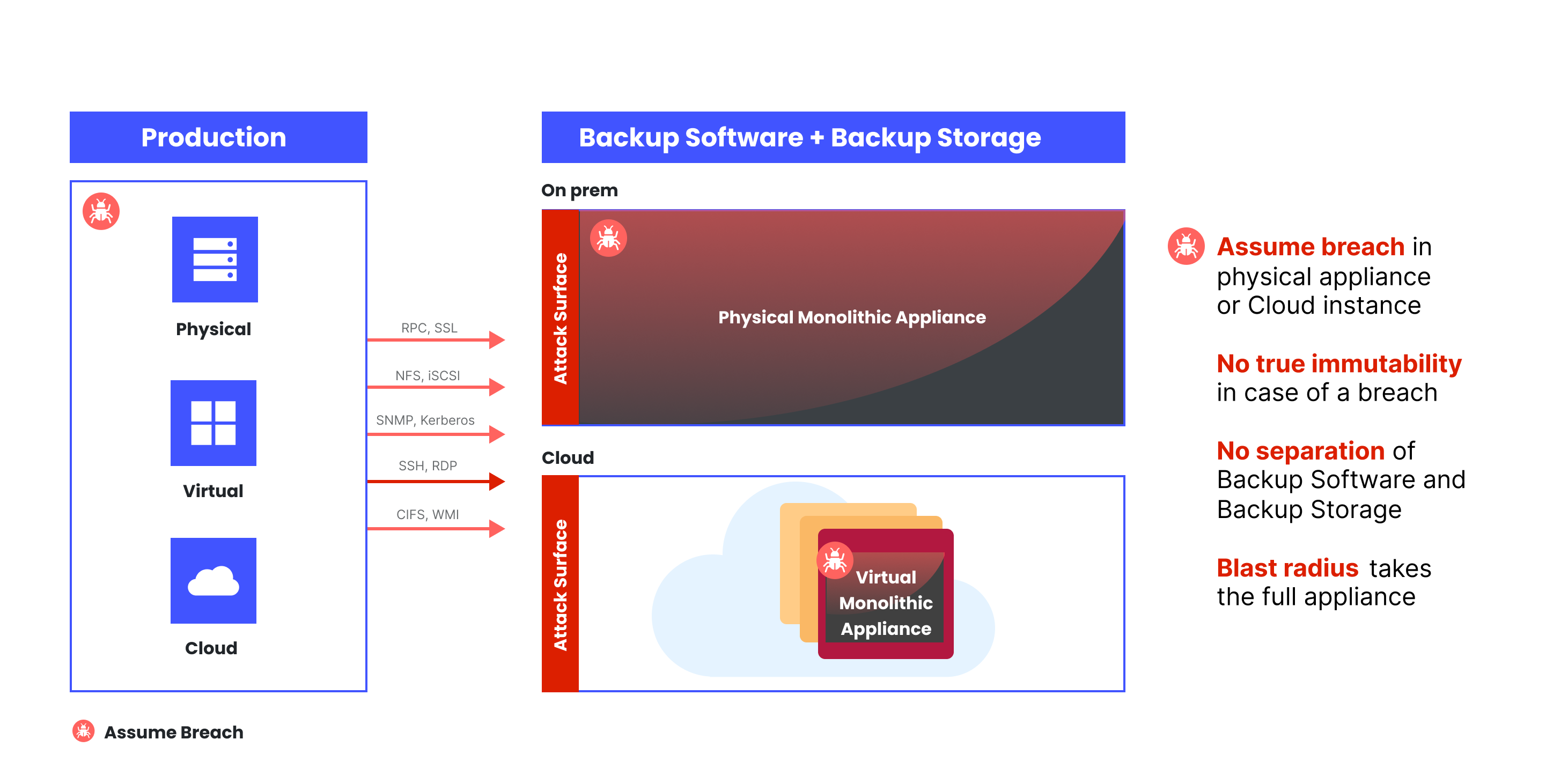
Figure 2: Monolithic appliances lack segmentation
This approach places too much trust in the vendor's proprietary file system immutability and security with administrative privileges. Due to their naturally unsegmented nature and built around the concept of All-in-One, sacrifices must be made to make the parts work as a whole. A storage pool may be labeled immutable, but the box admin can still perform factory resets or administrative (or governed) deletes. Suppose a part of the system fails due to an attack, corruption, or flawed software update. In that case, the rest of the system may become inoperable. Even if data remains immutable during a failure, if it’s inaccessible, it’s not resilient data.
In addition, it’s essential to recognize that deploying a monolithic virtual appliance into a cloud instance falls short of ensuring true immutability in a hybrid cloud scenario. In the event of a breach, where OS, instance, or account level credentials are compromised, the entire virtual appliance becomes susceptible, expanding the blast radius. The security vulnerability stems from performing data backup into the proprietary storage housed within the cloud-based virtual appliance. This weakness — caused by architectural misalignment with ZTDR — could be solved by backing up data directly into immutable cloud object storage external to the instance.
Direct Attached Storage, Old School and Out of Date
Direct-Attached Storage (DAS) is a commonly used storage architecture in many organizations. However, it poses a significant security risk as it does not offer immutability. It is directly attached to the backup server, with no separation between backup software and backup storage. This means that if an attacker gains access to the host by exploiting an OS or application vulnerability, they can easily access all the data on that system (see Figure 3).
With DAS, there is no mechanism to prevent unauthorized access or tampering with the data stored on the backup server. This makes it vulnerable to internal and external threats, including malicious insiders, cybercriminals, and hackers.
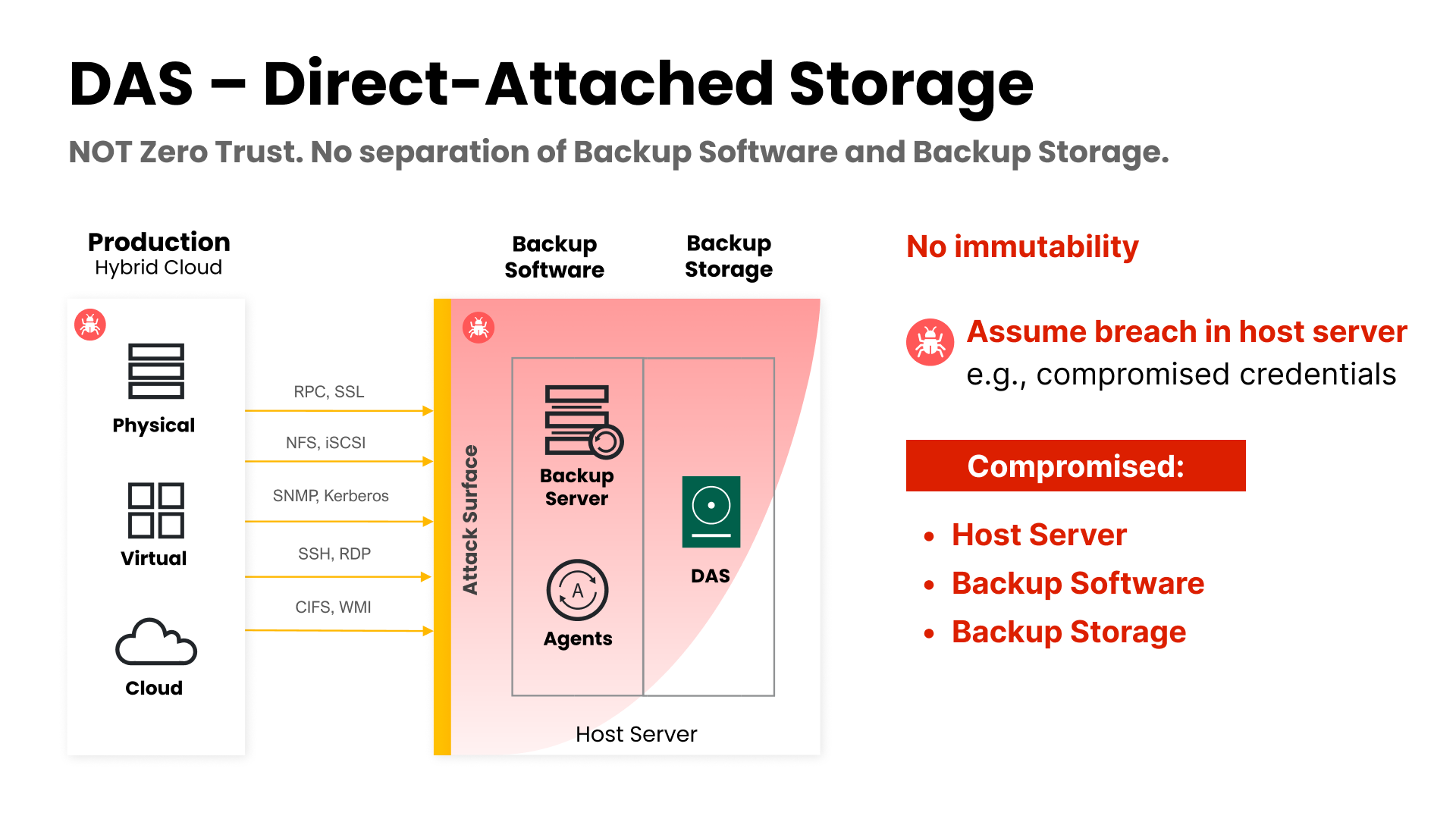
Figure 3: DAS lacks immutability and can be easily compromised.
While Direct-Attached Storage may seem like a convenient and cost-effective solution for backup and recovery, it poses significant security risks that should not be ignored. By implementing a backup storage architecture that provides immutability and separation of backup software and backup storage, organizations can significantly reduce the risk of data breaches and ensure the integrity of their backup data.
Other Storage Options
The same considerations apply to other storage types, such as dedupe appliances, NAS, or even a build-your-own Veeam Hardened Linux Repository. While each has its strengths as storage targets like more capacity, independently managed, or simple convenience, they also lack the security required to be considered Zero Trust Data Resilient. When considering these devices for backup storage, ask these questions:
- Is the storage hardened by default (out-of-the-box)?
- Does it require additional security expertise or training to configure and manage?
- Does administrative privilege grant access for deletes or resets?
- Will this minimize my attack surface and be able to operate without my backup software?
- What kind of immutability is being used, governance (admins can delete) or compliance (no one can delete)?
Final Thoughts
Security breaches are no longer a matter of if but when. Organizations must proactively safeguard their systems and data against potential threats.
In this blog series, we covered Zero Trust Data Resilience principles proposed by Veeam and Numberline Security, extending Zero Trust to Enterprise Backup systems. By embracing the principles of Zero Trust Data Resilience, organizations can have a clear and concrete pathway to strengthening their backup and recovery system security posture. This approach enhances the traditional Zero Trust maturity model. It ensures that backup infrastructure is securely segmented into multiple data resilience zones, the attack surface is minimized, least-privileged access is enforced for each zone, and it leverages immutability to protect backup data from modification and deletion regardless of administrative privilege.
In addition, ZTDR promotes more efficient operations and alignment between backup admins, IT, and security teams, ultimately leading to a faster and safer recovery in the event of a breach. By implementing these best practices, organizations can demonstrate their commitment to security and build trust with their customers and stakeholders. To learn more, please read our whitepaper and the original research paper written by Jason Garbis and Veeam.



