Object First (Zero) Trust Center
How Much Should You Trust
Your Storage Vendor?
If you are familiar with the concepts of Zero Trust, you already know to assume breach and reduce access when it comes to your people, process, and technology. For anyone associated with data protection, these concepts are core to keeping your organization, its data, and your customers’ data secure.
Whether you are security-conscious, healthily skeptical, or just plain curious, we want to deserve your trust and sincerely seek to help our extended community improve its security posture, whether using our solutions or not.
In the Object First Trust Center, you will find transparent disclosures regarding our compliance, privacy, and security practices.
If you read something and have any questions or concerns, please contact us at [email protected].
A Zero Trust Primer
Assume Breach!
You have probably heard a thing or three about Zero Trust recently, but if you haven’t, here’s a two-sentence primer:
Zero Trust is a security principle based on not trusting any entity — inside or outside the network — by default. The constant assumption that you could be and will be breached at all times creates a healthy level of preparedness that forces continuous verification of the identity and security status of all users, devices, and applications, regardless of location or network connection.
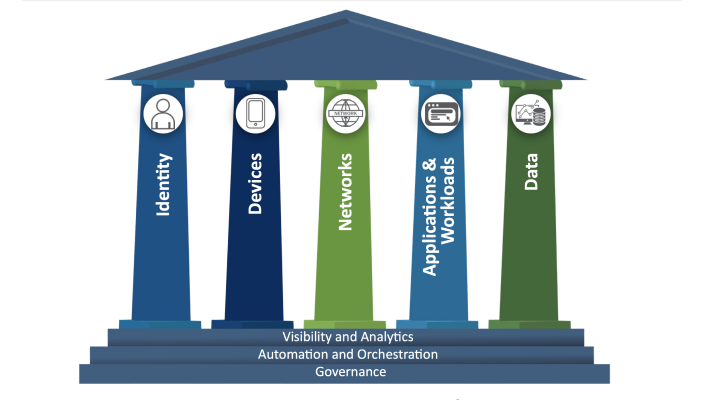
CISA Zero Trust Maturity Model
The Zero Trust maturity model, pioneered by agencies like CISA and NIS2, has become the gold standard for modern software security. The Zero Trust maturity model is a framework that encourages a comprehensive approach to security by assuming no entity is trustworthy by default and mandates continuous verification of all users, devices, and applications within an organization.
Zero Trust Data Resilience (ZTDR)
While an essential foundation, the Zero Trust Maturity Model does not consider Backup Software and Storage as part of its coverage framework. Veeam and Numberline Security published a research paper introducing a new model called Zero Trust Data Resilience (ZTDR) to extend this thinking to the backup and recovery use case.
What’s essential to take away from this effort is that Zero Trust and Zero Trust Data Resilience are an ongoing effort, not a single exercise you can complete and move on. Hardening and software security, identity and access management, security awareness training, and disaster recovery preparedness must all be considered, deployed, tested, and constantly updated as an ongoing process. Implementing a Zero Trust Data Resilience strategy can seem daunting, but it starts with simply understanding the three ZTDR pillars:
-
Segmentation — Separation of Backup Software and Backup Storage to enforce least-privilege access and minimize the attack surface and blast radius.
-
Multiple data resilience zones or security domains to comply with the 3-2-1 Backup Rule and to ensure multi-layered security.
-
Immutable backup storage to protect backup data from modifications and deletions. Zero access to root and OS, protecting against external attackers and compromised administrators, is a must-have as part of true immutability.
We encourage everyone to read the entire research paper to help them fully understand the need to address critical gaps in their backup infrastructure proactively.
Zero Trust Data Resilience defines best practices for securing backup software and backup storage, and Ootbi was engineered with these practices at its earliest phases of development. A significant concept of any trust model is to get the job done securely and efficiently. While security is important for many, it is often not at the forefront of priorities when it comes to backup storage. That is not the case for Object First Ootbi.
Operational Security
Product Design
When designing Ootbi, we wanted to create something that was not only secure, simple, and powerful but that operated entirely independently from Veeam without the need for admin oversight, custom security policies, or additional optimizations. This design mindset highlights the importance of separating the backup storage from the backup software; Ootbi’s appliance form factor allowed us to reduce the attack surface and build something that helps to create carefully defined network security access, all configured by default:
- Layer 1:
Storage designed for operation with immutable backups - Custom-engineered object storage software tuned for the latest security best practices purpose-built for Veeam.
- Layer 2:
A Hardened Linux operating system that is pre-configured and secured to ensure a foundational security posture. More importantly, we deny device owners access to the root account, operating system, and object store to maintain a least-privileged Zero Trust approach.
- Layer 3:
Locked-down hardware form factor means physical destruction is the only means of harming data. Without physical access the immutable data on the appliance remains impenetrable.
Minimized Attack Surface
The layered approach allows us to tailor our operating environment further to focus explicitly on ensuring security is always the top priority. Even when your environment is breached:
- No additional software can be installed on the device.
- Ootbi continuously monitors for configuration changes.
- The “Fail to ban” approach means continuous bad logins will create a system lockout, and administrators will be notified via email.
Another way we ensure your attack surface remains small is with verified updates provided directly by Object First. Kernel and software updates are curated by Object First and procured directly from Object First servers. If it doesn’t come directly from us, it will not work with your Ootbi appliance.
Product Security
As mentioned in the Zero Trust section, Ootbi was built around Zero Trust Data Resiliency Principles. Due to our hardware form factor, we are inherently segmented from backup storage, which is secure out of the box by default. We will always maintain our security through proactive testing and updates.
Secure by Default, Secure Always
Because we are Zero Trust, we don't trust any entity by default, even if it's inside the network perimeter. We leverage Zero Trust principles to ensure your system is secure at every operating and service state. Our system is designed to continuously monitor configurations and security settings, automatically resetting them to their expected state if any changes occur. This proactive stance ensures that your system remains resilient to evolving threats.
Our commitment to security extends to access control. We take a bold step by keeping SSH off by default, granting access only through a limited Text User Interface (TUI) when necessary. No root access via SSH or otherwise is allowed, providing additional protection against unauthorized access.
Insider Defense
Insider protection is not just about safeguarding against malicious actors but also about preventing honest mistakes. Ootbi is engineered to detect and prevent both, ensuring your system remains secure from all angles. Any failed attempt to log into the device will generate a notification that is sent to device admins, and all login/logout activity is tracked. Ootbi updates are all-inclusive and curated to keep all software and system components optimized and secure. All update repositories are hosted by Object First, ensuring a seamless and trustworthy update process.
We prioritize access verification to the highest degree. Even the most privileged admin cannot inadvertently destroy critical data. Multi-factor authentication (MFA) options further fortify your system against unauthorized access attempts.
Security by Segmentation
While we encourage you to manage physical security, Ootbi takes the lead in securing your digital assets. We incorporate Veeam's Trust and Security principles for added peace of mind. Using Ootbi as a target for encrypted configuration backups means recovery is always an option, even when the backup software is compromised. Veeam encrypted data would remain encrypted regardless of whether the data were exfiltrated.
We secure communication with HTTPS/TLS, mitigating time skew issues. This means every aspect of integration between Veeam and Ootbi is secured, which helps further separate and create additional recovery vectors in worst-case scenarios.
An Ongoing Effort
Our commitment to ongoing security is unwavering. Constant third-party security testing ensures that we stay ahead of emerging threats.
We recently employed the expertise of the NCC Group, a team of cybersecurity experts, to conduct comprehensive penetration tests on the Ootbi appliance and its software to help us identify and address undiscovered risks. Read the full report here.
Secure by Design
The CISA Secure by Design pledge encourages organizations to integrate security measures from the outset, embedding them deeply within their design and development processes to enhance their overall cybersecurity posture. Object First has signed CISA’s Secure by Design pledge and posted our progress on accomplishing the seven steps outlined in the pledge here.
Privacy and Compliance
At Object First, compliance meets credibility. We understand the paramount importance of adhering to regulations, and we're proud to assure our clients that our practices align seamlessly with the most stringent standards.
Object First is:
CCPA Complaint:
The CCPA (California Consumer Privacy Act) ensures that consumers in California have the right to know what personal information is being collected about them, the right to delete personal information held by businesses, and the right to opt out of the sale of their personal information.
GDPR Compliant:
The GDPR (General Data Protection Regulation) enhances the protection of personal data for individuals within the European Union, granting them greater control over their personal information through rights such as access, rectification, deletion, and the right to object to data processing.
Vulnerability Reporting
At Object First, we deeply value the security and integrity of our systems. This is why we have implemented a robust vulnerability reporting process that underscores our commitment to acting responsibly and swiftly upon discovering security risks. We take any findings incredibly seriously, recognizing the contributors who discover vulnerabilities as vital partners in our ongoing effort to secure and improve our offerings.
Our expert team analyzes each report to ensure appropriate measures are taken to address and mitigate vulnerabilities. Our goal is to resolve issues promptly and foster an environment of transparency and trust with our customers, appreciating their crucial role in helping us maintain the highest security standards.
If you have found a vulnerability or want to contact us about a concern, please read our Vulnerability Reporting Policy and contact us at [email protected].