Il Repository Sicuro di Object First per Veeam: Ootbi e Sicurezza IT
Come Applicare un Design Sicuro all'Architettura di Protezione dei Dati
Perché qualcuno dovrebbe salire su un aereo? Dopotutto, viaggiare a 600 mph a un'altitudine di 40 mila miglia in una lattina altamente infiammabile sembra essere il modo di trasporto meno sicuro.
Eppure, tutti sanno che il contrario è vero. L'aviazione sfida una moltitudine di minacce raddoppiando gli sforzi per la sicurezza. Di conseguenza, volare è ufficialmente la forma di viaggio più sicura.
Puoi fare un'affermazione simile riguardo alla tua architettura di protezione dei dati?
Sicurezza IT e Backup
In questo articolo, esamineremo la sicurezza IT nell'architettura di backup come un processo continuo che deve essere costantemente rivisitato.
Poiché le minacce cambiano e si adattano, nessuna misura di sicurezza può essere data per scontata come una soluzione universale. Ecco perché in Object First seguiamo specifici framework per assicurarci che Object First Ootbi (Out-of-the-box Immutability) non sia solo il miglior storage per Veeam, ma anche conforme agli ultimi standard di sicurezza, rimanendo costantemente sicuro, semplice e potente.
Continua a leggere per scoprire di più sul nostro processo e sulla sicurezza del backup in generale.
Quanto è Sicuro il Tuo Repository di Backup Veeam?
Se ti senti avventuroso e vuoi testare la sicurezza del tuo backup, prova questo esercizio: invia email di phishing false ai tuoi dipendenti e vedi quanti cadono nella trappola. È probabile che non siano zero.
Un sistema non è sicuro quando non può mai essere violato, ma quando è progettato tenendo a mente le violazioni.
Dal punto di vista della sicurezza IT, non importa se le persone cliccano sul link malevolo in una simulazione di phishing. Ciò che conta è prepararsi per quando lo faranno, implementando precauzioni personalizzate esplicitamente progettate per contrastare questo tipo di incidente.
Questo è il dominio della sicurezza IT: sviluppare strategie per prevenire e mitigare potenziali incidenti sui dati, come il ransomware.
Oh, giusto, ransomware: l'arcinemico dei backup. Sapevi che il ransomware prende di mira i backup 9 volte su 10? I criminali sanno che non verranno pagati se puoi ripristinare i dati che hanno crittografato per riscatto.
Tuttavia, la crittografia o la distruzione è solo ciò che il ransomware fa una volta penetrato il perimetro.
Per essere veramente a prova di ransomware, non aspettare di dover fermare la crittografia. Segmenta l'infrastruttura per contenere l'infiltrazione.
Come Può Essere Consegnato il Ransomware?
Questa domanda dovrebbe sostenere il design di ogni repository di backup a prova di ransomware. Possiamo usarla per anticipare vari modi in cui il ransomware può entrare nei nostri sistemi. Questi modi possono includere:
- Ingegneria sociale, nota anche come phishing, può assumere molte forme: una buona vecchia email, un pop-up, una telefonata o persino un clone Wi-Fi.
- Minacce interne. I dipendenti scontenti sono una forza crescente dietro gli incidenti di sicurezza. Infatti, le minacce interne rappresentano il 31% delle violazioni dei dati.
- Credenziali rubate. Secondo un rapporto di Mandiant, il 40% degli attacchi ransomware nel 2023 ha utilizzato credenziali compromesse come vettore d'attacco.
- Errore umano. L'evergreen delle responsabilità e dell'errore umano è sempre presente nella lista dei principali rischi per la sicurezza.
I progettisti e gli ingegneri devono identificare queste e altre minacce alle loro infrastrutture di backup e seguire con soluzioni efficaci. Solo allora possono creare un dispositivo di backup robusto e sicuro.
Migliori Pratiche per i Dispositivi di Backup
Ootbi, che sta per immutabilità out-of-the-box, è un dispositivo di backup progettato appositamente per Veeam dai fondatori di Veeam.
Dalla nostra lancio nel 2022, il ransomware rimane una preoccupazione principale per gli specialisti IT, e i backup rimangono il modo migliore per proteggere i tuoi dati.
Tuttavia, gli attori delle minacce e i loro metodi si sono evoluti. Per tenere il passo, ci stiamo evolvendo con loro.
Ad esempio, l'immutabilità è sempre stata il nostro valore fondamentale. Tuttavia, alla fine, abbiamo dovuto chiederci: l'immutabilità da sola affronta le attuali sfide di sicurezza, o dovremmo aggiungere qualcosa per tenere conto di altre minacce?
L'Immutabilità è Sempre una Cosa Positiva?
Sì, stiamo essendo provocatori. Dopotutto, l'immutabilità è sempre stata vitale per la nostra attività. È persino nel nome del nostro prodotto.
D'altra parte, il termine "immutabilità" ha dominato così completamente il discorso nella cybersecurity che potrebbe farci diventare ciechi ad altre minacce, quelle che l'immutabilità non può affrontare.
Ricorda: l'immutabilità è solo l' ultima linea di difesa. Quando impedisce a un agente malevolo di crittografare i tuoi backup, c'è a malapena motivo di festeggiare. Quell'agente si aggira intorno ai tuoi locali da un bel po' di tempo. Tutte le altre difese sono fallite, il che significa che la sicurezza dei tuoi dati pende dal sottile filo dell'immutabilità da solo.
Quando l'immutabilità ferma il ransomware, significa che tutte le altre difese hanno fallito. Non fare affidamento sulla sicurezza dei tuoi dati solo sull'immutabilità.
È come se la tua unica garanzia di sicurezza a bordo di un aereo in volo fosse un piccolo paracadute avvolto precariamente attorno alle tue braccia.
Modellazione delle Minacce e Principi di Design Sicuro
Entrano in gioco la modellazione delle minacce e i principi di design sicuro. Questi framework di sicurezza sono stati sviluppati da OWASP, The Open Worldwide Application Security Project, un'organizzazione benefica internazionale con due decenni di esperienza nella promozione dei migliori standard di sicurezza.
Qual è lo scopo della modellazione delle minacce e dei principi di design sicuro?
OWASP ha sviluppato la modellazione delle minacce e i principi di design sicuro per aiutare gli ingegneri a dotare i loro sistemi di meccanismi di difesa potenti, pertinenti ed efficaci.
Gli ingegneri utilizzano la modellazione delle minacce e i principi di design sicuro come ispirazione per ideare meccanismi di difesa.
Questi meccanismi non devono essere arbitrari. Non esiste un elenco di "10 cose che ogni sistema deve avere per essere sicuro". Invece, la modellazione delle minacce e i principi di design sicuro sono raccomandazioni, o suggerimenti. I progettisti e gli ingegneri utilizzano questi suggerimenti per sviluppare misure di sicurezza specifiche per le loro esigenze. Ad esempio, possono estendere il loro arsenale di difesa contro il ransomware oltre l'immutabilità.
Esaminiamo i due framework di sicurezza e la loro applicazione al backup, iniziando dalla modellazione delle minacce.
Cos'è la modellazione delle minacce nella cybersecurity?
Nella cybersecurity in generale e nel design dell'architettura di backup in particolare, la modellazione delle minacce ruota attorno a quattro domande chiave. Gli ingegneri le pongono prima di sedersi al tavolo da disegno. Idealmente, però, non smetteranno mai di porle.
La sicurezza IT è un processo continuo, quindi le quattro domande non possono mai avere una risposta definitiva.
La modellazione delle minacce pone domande a cui non puoi mai dare una risposta definitiva. La sicurezza IT è un obiettivo in movimento, quindi le risposte cambieranno sempre.
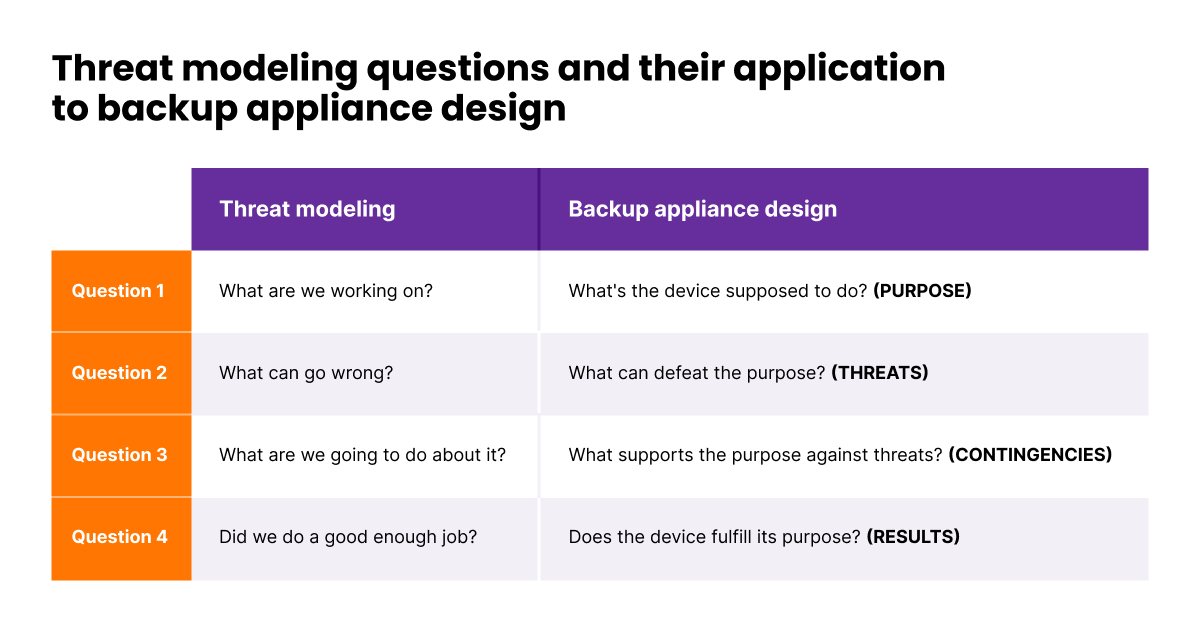
Fig. 1. Domande sulla modellazione delle minacce e la loro applicazione al design del dispositivo di backup
Nota che abbiamo reso tutte le domande riguardanti il scopo. Questo perché lo scopo è la nostra misura ultima di successo e un principio chiave dietro il design e l'esecuzione in Object First.
Inoltre, l'esperienza ci dice che uno scopo chiaramente definito aiuta a rispondere in modo più accurato alle altre domande della modellazione delle minacce.
Come Fare la Modellazione delle Minacce per i Backup?
Uno sguardo più da vicino alla nostra descrizione del prodotto renderà evidente il nostro scopo nella creazione di Ootbi:
A prova di ransomware e immutabile out-of-the-box, Ootbi di Object First offre storage di backup sicuro, semplice e potente per i clienti Veeam.
La descrizione del prodotto evidenzia l'immutabilità, l'integrità dei dati e la resilienza al ransomware come le principali caratteristiche di sicurezza di Ootbi.
Ora, il modello di minaccia ci costringe a considerare: Cosa può minare l'immutabilità di Ootbi? Cosa può compromettere la sua integrità dei dati? Cosa può ridurre la sua resilienza al ransomware?
Con un mix di immaginazione ed esperienza, elaboriamo scenari di minaccia plausibili. Poi, è tempo di ricercare, ideare, ingegnerizzare e implementare soluzioni per mitigare quegli scenari.
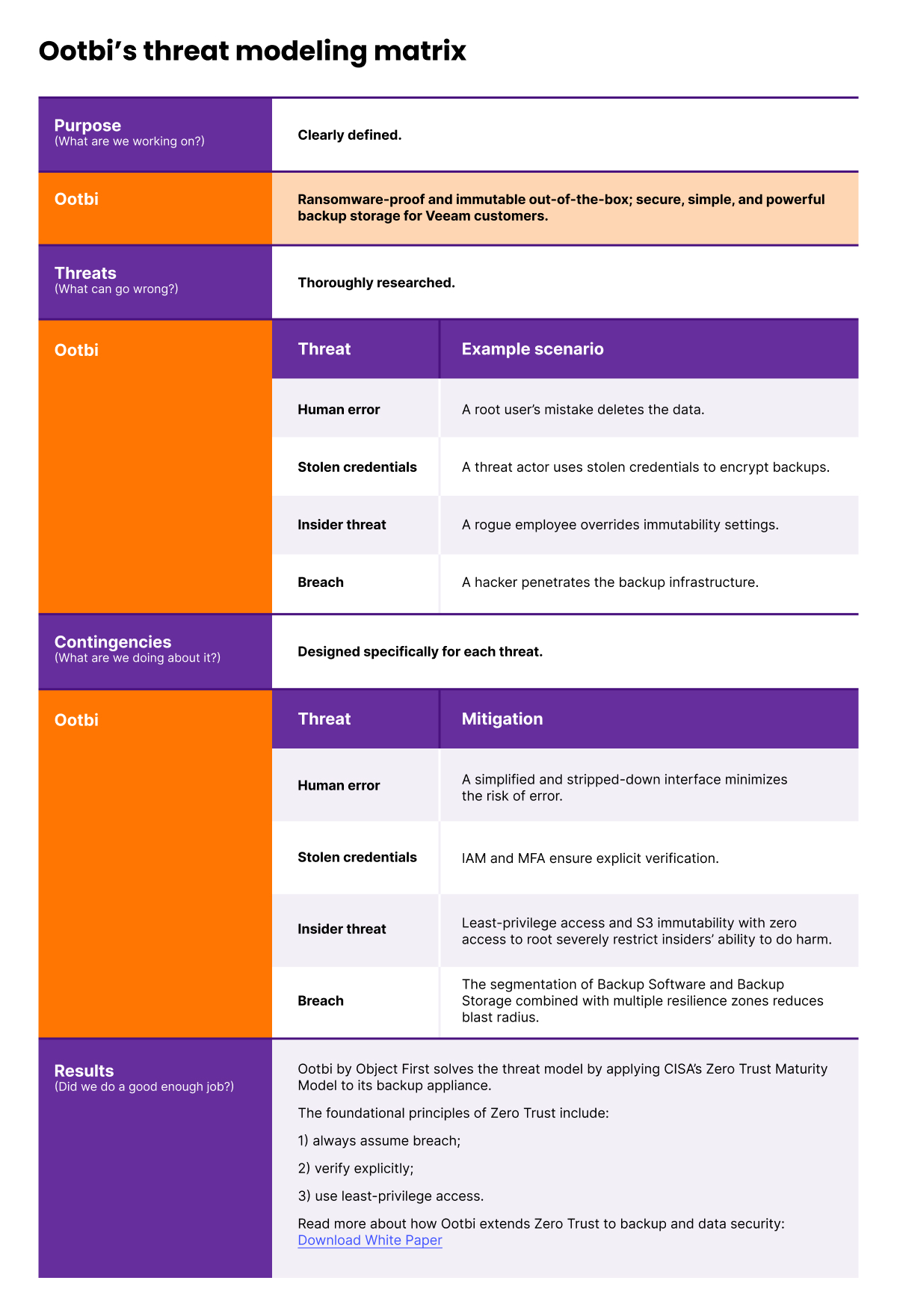
Fig. 2. Matrice di modellazione delle minacce di Ootbi
Passiamo ora all'altro framework sviluppato da OWASP: principi di design sicuro.
Quali Sono i Principi del Design Sicuro?
Come la modellazione delle minacce, i principi di design sicuro supportano la creazione di prodotti sicuri. Tuttavia, mentre la modellazione delle minacce offre un insieme di domande aperte, i principi di design sicuro sono un po' più prescrittivi.
Ogni principio affronta un particolare rischio di sicurezza. Questi rischi sono in gran parte universali. Ad esempio, evitare un singolo punto di compromesso completo sembra ragionevole sia che tu stia costruendo un dispositivo di backup o un aereo.
Le raccomandazioni di design sicuro sono universali sia che tu stia costruendo un dispositivo di backup o un aereo.
Per ogni rischio di questo tipo, i principi di design sicuro propongono una raccomandazione ampia, ad esempio, “Un singolo punto di compromesso completo può essere evitato con più controlli di sicurezza.” Tuttavia, quali controlli di sicurezza vengono utilizzati e come dovrebbero essere implementati è una questione di scelta e meglio lasciata a esperti di sicurezza esperti.
I principi non prescrivono implementazioni specifiche. Questa decisione è meglio lasciata agli esperti di sicurezza.
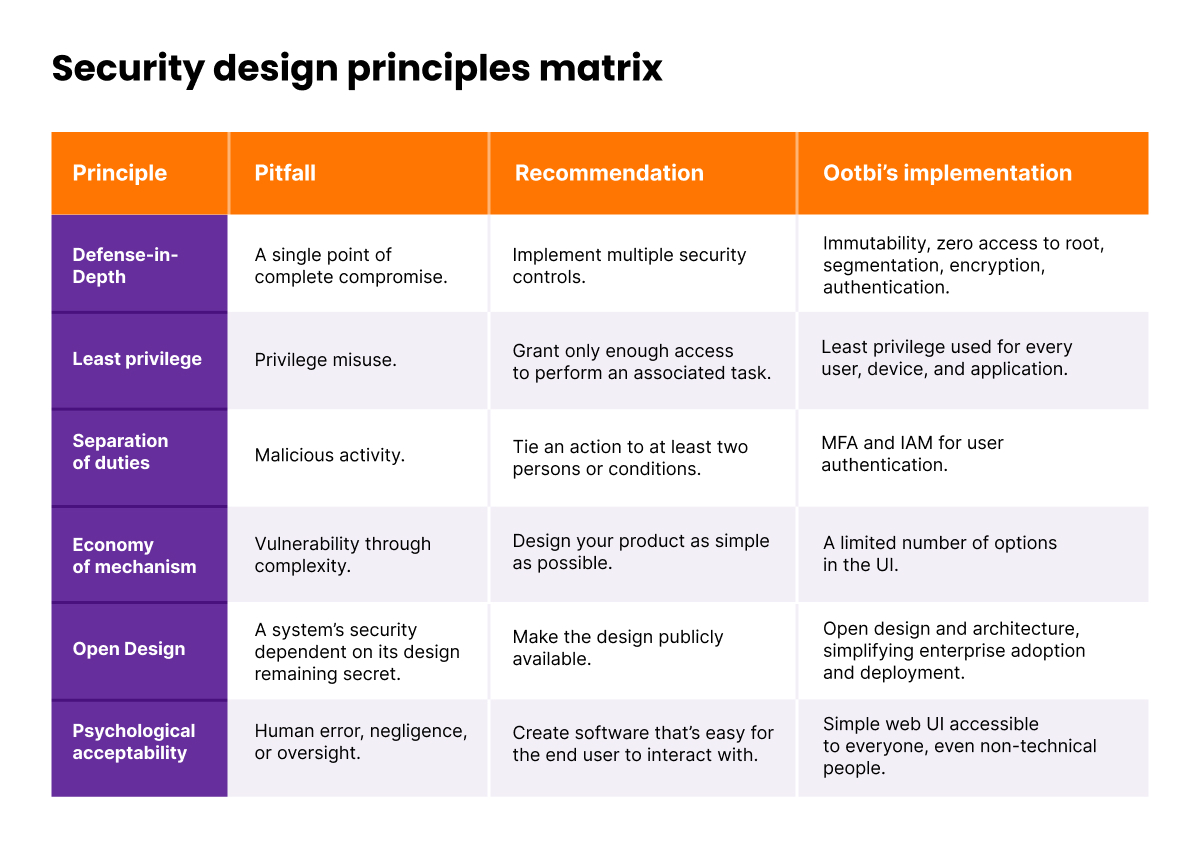
Fig. 3. Matrice dei principi di design sicuro
Ootbi: Costantemente Verificato da Esperti del Settore
Teoricamente, tutto ciò di cui hai bisogno per i backup è Linux e storage. Combina i due con un po' di magia da amministratore, e ottieni un repository Linux rinforzato.
Il tuo repository Linux rinforzato sarà altrettanto rinforzato tra un anno?
Gli aerei sono prodotti sotto supervisione e secondo standard di costruzione. Sottopongono regolarmente a manutenzione, controlli di sicurezza e aggiornamenti. Non ti aspetteresti di volare in un aereo fai-da-te anche se avessi un manuale di istruzioni e un paracadute da abbinare.
Come l'aviazione, la sicurezza dei dati non è per chi ha una mentalità fai-da-te. Se ti interessa i tuoi backup, c'è solo un modo per essere sicuri che siano esattamente sicuri tra un anno come lo sono oggi: assumere professionisti.
Object First applica continuamente la modellazione delle minacce e i principi di design sicuro a Ootbi.
Object First applica la modellazione delle minacce e i principi di design sicuro a Ootbi in modo continuativo. Rilasciamo aggiornamenti software e offriamo supporto 24/7 in modo che l'utente non debba pensare a configurazione, manutenzione o adattamento al panorama delle minacce in continua evoluzione. Facciamo tutto questo per loro.
Richiedi una demo oggi e scopri come Ootbi di Object First mantiene continuamente gli ultimi standard di sicurezza. Con Ootbi, il repository più sicuro per Veeam, non devi preoccuparti se la tua architettura di protezione dei dati è aggiornata: lo è sempre.



