Introducing Object First’s Honeypot Feature
Backup environments are a key target on a ransomware attacker’s agenda. Attackers know that if your backups survive, you are less likely to pay the ransom. That’s why backup servers, including Veeam Backup & Replication (VBR) are often the first systems they try to disable.
To help backup administrators monitor these threats, Object First has released a honeypot feature in our Ootbi (Out-of-the-Box Immutability) 1.7 release. This feature is designed to assist in the early detection of suspicious activity targeting backup infrastructure without adding complexity or overhead to your administrative tasks.
What’s a Honeypot?

Image Courtesy of Western Washington University and designed by Zeck Koa and Chris Baker.
As bees are drawn to nectar, so bad actors are drawn to vulnerable systems. Honeypots are decoy systems that are real servers, operating in isolated and monitored environments. They’re intended to attract attackers and alert you when someone is probing your environment. Think of it as a tripwire. It’s a way to become aware of threat activity before they escalate into a catastrophe.
Ootbi’s Honeypot feature simulates a VBR production server, complete with open ports that attackers typically look for (like SSH, RDP, SQL Server, and VMware). When someone scans or tries to access it, the system immediately generates alerts.
This is especially useful during the dwell phase of an attack—when intruders have gained access to the environment and are stealthily exploring your network before launching a full-scale assault. Detecting them early can prevent a successful ransomware attack.
How to Enable the Feature
Most honeypots are custom, unsupported toolkits that are complex to set up and operate. Existing toolkits can take 30–50 steps to configure, which often deters administrators from deploying them.
Conversely, Ootbi's Honeypot is designed for ease of use and monitoring. The feature is built into all Ootbi appliances and can be easily turned on in five steps:
1. Log into the Cluster Manager UI of your Object First appliance.
2. Navigate to Settings > Security > Honeypot.
3. Check the box to Enable Honeypot.
4. Choose your IP mode:
- DHCP: Automatically assigns an IP address.
- Static: Manually set an IP and netmask.
5. Click the “Apply Changes” button.
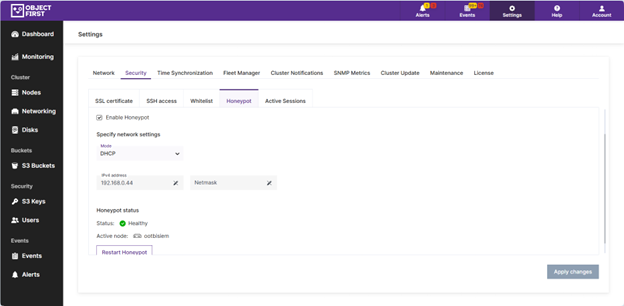
That’s it. In just a few clicks, you’ve deployed a fully functional honeypot. Even if you opt for a static IP configuration, setup rarely exceeds five clicks once you’re in the Cluster Manager.
How Alerts Work—and Where They Go
Once the honeypot is active, it begins monitoring for abnormal activity. This includes:
- Multiple authorization attempts
- Port scans
- Probing behavior
- Requests on sensitive protocols
- Service startup failure
- Unexpected service stop
- Service failure
- Suspicious Veeam Console access
- Cumulative suspicious activity
- Service lifecycle events (start/stop) – informational
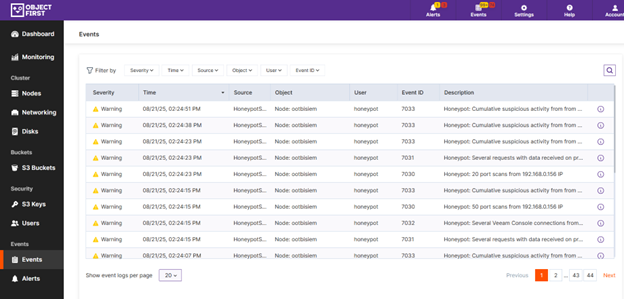
Alerts are visible in Ootbi Cluster manager, and can be sent through Object First’s standard notification system, which supports:
- Email (SMTP): You’ll need to specify your email server.
- Syslog: For integration with SIEM platforms like Splunk or ELK.
Each alert includes key details like:
- Event ID (e.g., 7041 for SSH attempts, 7030 for port scans)
- Source IP address
- Protocol targeted
- Summary of activity
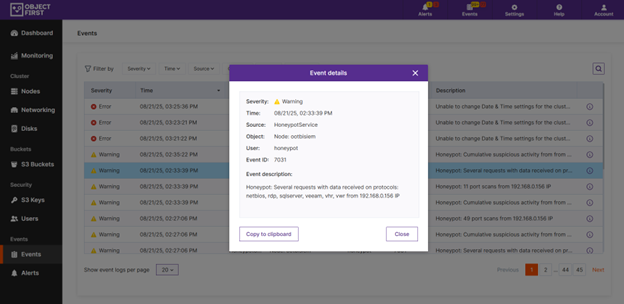
As depicted above, you can view alerts directly in the Object First dashboard.
Real-World Use Cases
Whether you’re a solo IT admin or part of a larger team, the honeypot feature can offer immediate benefit to your team:
- Small teams: If you wear multiple hats—backup, security, infrastructure—you’ll appreciate the simplicity. You’ll gain insight into suspicious activity without needing to be a security expert.
- Larger organizations: Backup admins can use honeypot alerts to begin discussions with security teams. “Are you scanning my systems?” If not, it’s time to investigate.
Even internal misbehavior—like junior staff running unauthorized scans—can trigger alerts. This feature's benefits extend beyond catching bad actors. It helps the team build security awareness and best practices response protocols.
What It’s Not
Let’s be clear: this is not an EDR (Endpoint Detection and Response) system. It’s not a replacement for your existing security tools.
Instead, it’s a value-add: a lightweight, easy-to-use feature that helps you detect threats early and respond faster. It’s another tool in your toolbox, not one that replaces others.
Final Thoughts
Setting up your cybersecurity defenses can be a complex process, but your everyday tools shouldn’t be. With Object First’s Honeypot feature, you can easily add more defense in depth, getting powerful early detection capabilities without the burden of setup, maintenance, or deep security expertise.
It’s simple. It’s effective. And it’s built to make your life easier.



